Intelbroker’s Hewlett Packard Enterprise (HPE) Data Breach
The cybersecurity landscape was shaken once again when Intelbroker, zjj, and EnergyWeaponUser threat actors, disclosed a significant data breach involving Hewlett Packard Enterprise (HPE).

The cybersecurity landscape was shaken once again when Intelbroker, zjj, and EnergyWeaponUser threat actors, disclosed a significant data breach involving Hewlett Packard Enterprise (HPE). The breach, which came to light on January 16, 2023, exposed sensitive internal data, including source code, certificates, and API access. However, the leaked configuration files and web service details provide even more insight into the potential risks and vulnerabilities that HPE now faces.
What Was Leaked?
- Service Configuration and Execution Details:
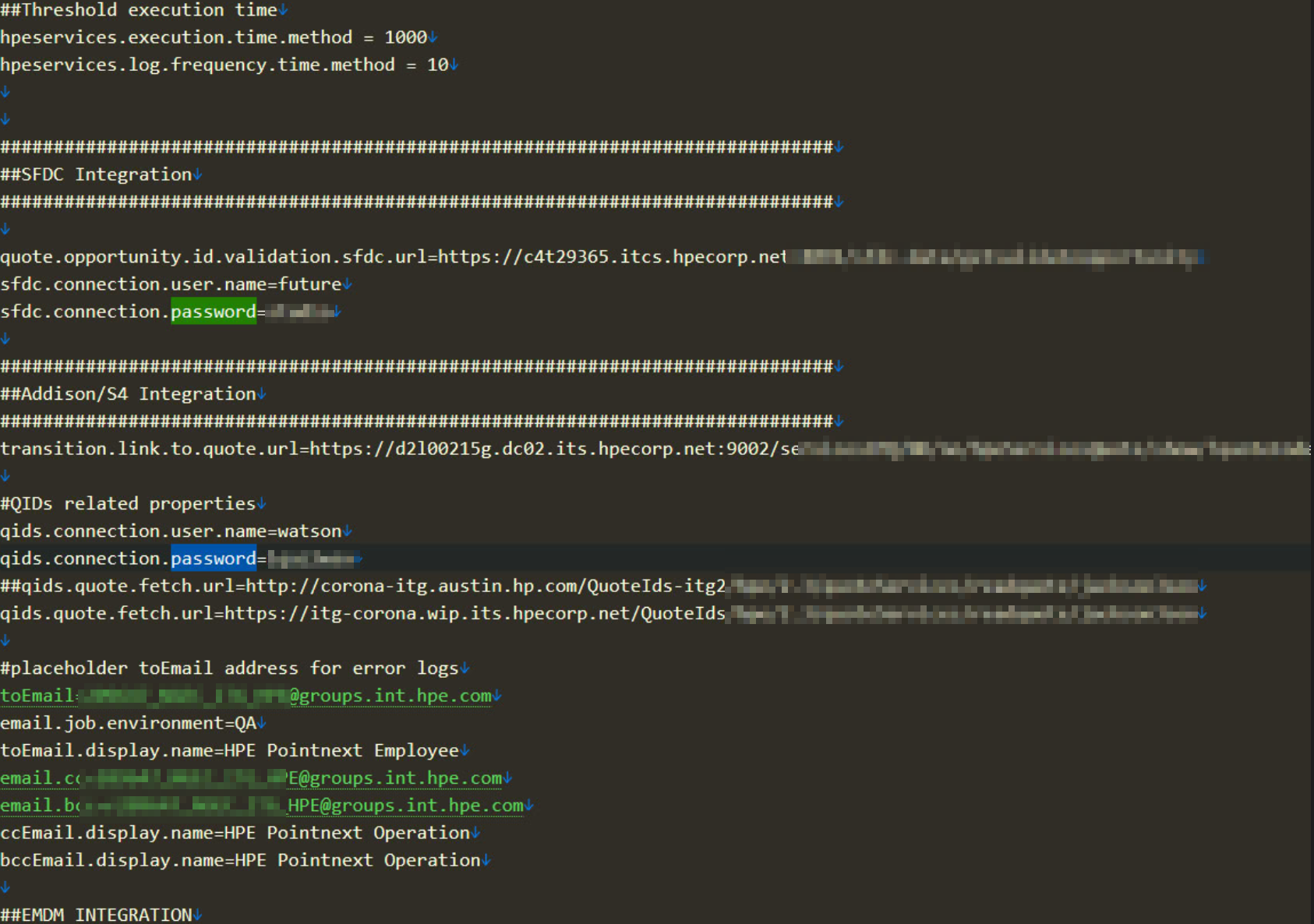
- The leaked files reveal critical operational parameters, such as execution time thresholds (
hpeservices.execution.time.method = 1000) and log frequencies (hpeservices.log.frequency.time.method = 10). These details are crucial for the smooth functioning of HPE’s internal systems and could be exploited to disrupt services or manipulate logs to cover malicious activities.
- The leaked files reveal critical operational parameters, such as execution time thresholds (
- Integration Credentials:
- The breach exposed integration details with Salesforce (SFDC) and other systems, including URLs, usernames, and passwords. For example:
- SFDC credentials:
sfdc.connection.user.name=future,sfdc.connection.password=studio - QIDs credentials:
qids.connection.user.name=watson,qids.connection.password=lqaz2wsz
- SFDC credentials:
- These credentials could allow attackers to gain unauthorized access to integrated platforms, potentially leading to further data exfiltration or system manipulation.
- The breach exposed integration details with Salesforce (SFDC) and other systems, including URLs, usernames, and passwords. For example:
- Web Service Endpoints:
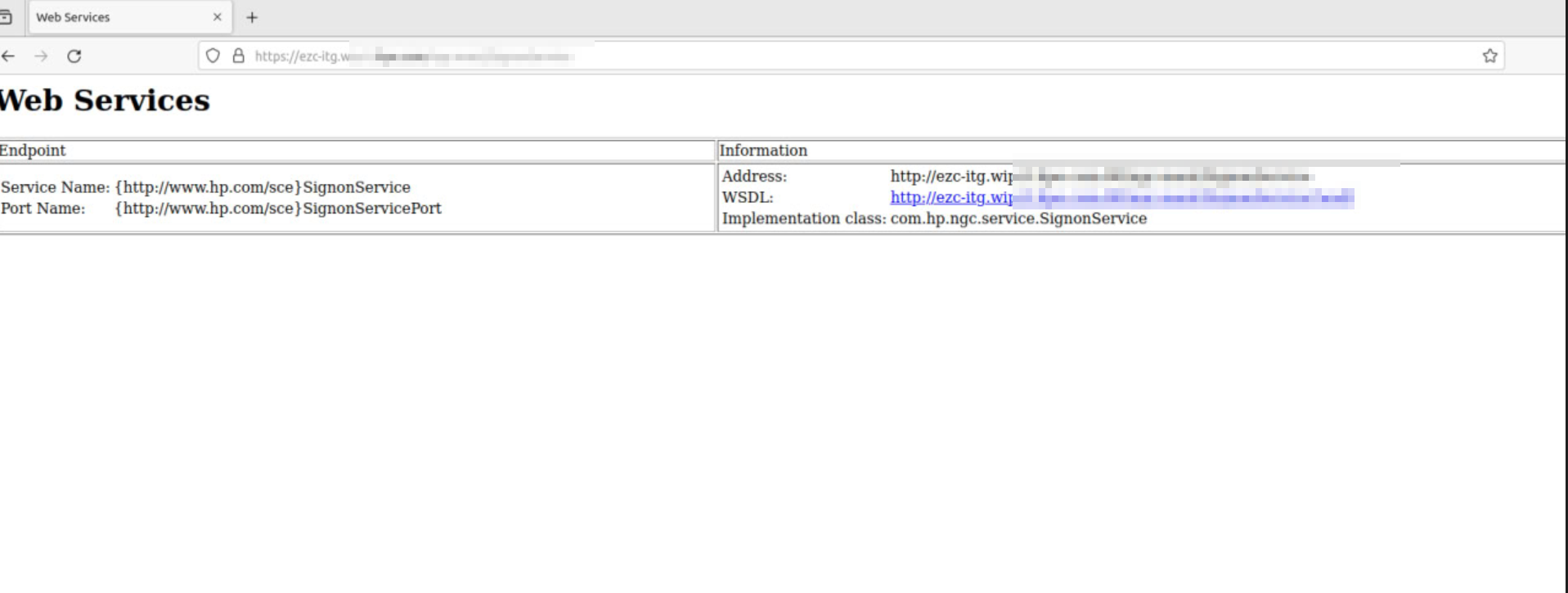
- Specific web service details, such as the
SignonService, were leaked, including the WSDL file location (http://src-tig.wip.it.ippe.com:80/npc-maul/SignonService?wsdl) and implementation class (com.hp.npc.service.SignonService). This information could be used to reverse-engineer or exploit these services.
- Specific web service details, such as the
- Email Configuration:
- The configuration files included email addresses and display names used for error logs and notifications. For example:
toEmail=209647_NGEC_ITG_HPE@groups.int.hpe.comemail.cc=209647_NGEC_ITG_HPE@groups.int.hpe.com
- This information could be leveraged for phishing campaigns or to gather more intelligence about HPE’s internal operations.
The Broader Implications
The exposure of such detailed internal information poses several risks:
- Credential Abuse: The leaked credentials could be used to access HPE’s integrated systems, such as Salesforce or internal quote management systems, leading to further data breaches or operational disruptions.
- Service Manipulation: With access to execution time and log frequency details, attackers could potentially manipulate system performance or cover their tracks by altering logs.
- Phishing and Social Engineering: The leaked email addresses and display names could be used in targeted phishing campaigns to trick employees into revealing more sensitive information or credentials.
- Reputational Damage: Beyond the technical risks, the breach could harm HPE’s reputation, especially if clients and partners lose confidence in the company’s ability to protect sensitive data.
While Intelbroker’s actions are undoubtedly concerning, they also highlight critical vulnerabilities that organizations like HPE must address. The breach is a stark reminder of the importance of robust cybersecurity practices, including regular credential rotation, enhanced monitoring, and thorough security audits.
Intelbroker’s disclosure, whether motivated by financial gain or other reasons, has revealed these vulnerabilities. While the breach is a serious incident, it also allows HPE to reassess and strengthen its security posture.




